Block cipher and stream cipher are symmetric encryption techniques that protect your data from unauthorized access. Symmetric encryption means the same key is used to encrypt and decrypt the data. In this blog post, I will explain block cipher vs stream cipher, their advantages and disadvantages, and some examples of each.
Stream Cipher
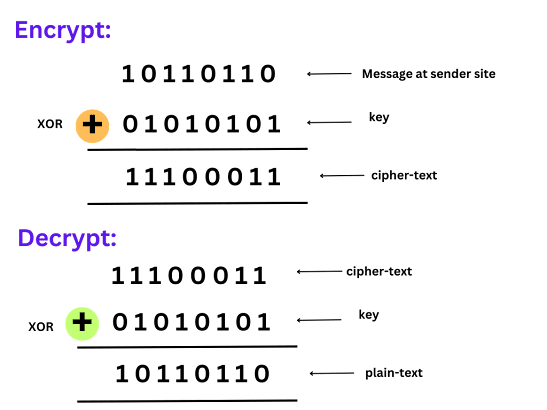
- The stream cipher encrypts the data by generating a stream of pseudorandom bits, called keystream, using a secret key and a nonce (a number used only once).
- The keystream is then combined with the plaintext using a bitwise XOR operator, and the result of (plaintext XOR key) produces a ciphertext stream.
- Stream cipher can also use different modes of operation, such as CFB (Cipher Feedback), OFB (Output Feedback), or Salsa20. Some examples of stream cipher algorithms are RC4, ChaCha20, and A5/1.
Advantages of Stream Cipher
- A stream cipher is faster than a block cipher, as it does not need to divide the data into blocks or perform complex transformations.
- Stream cipher also does not require padding, as it can encrypt any amount of data without changing its size.
- However, stream cipher also has some disadvantages. One is that it only provides confusion, not diffusion, making it less secure than block cipher against some attacks.
- Another is that each encryption requires a unique key and nonce combination; otherwise, the keystream will be repeated and the ciphertext will be compromised.
Block cipher
- A block cipher encrypts the data by dividing it into fixed-size blocks, usually 64 or 128 bits. Each block size should be the same.
- Each block is then transformed using a secret key and a cryptographic algorithm.
- The size of the ciphertext block should be the same as plaintext.
- Block cipher can use different modes of operation, such as ECB (Electronic Code Book), CBC (Cipher Block Chaining), CTR (Counter), or GCM (Galois/Counter Mode). Some most essential examples of block cipher algorithms are AES (Advanced Encryption Standard), DES (Data Encryption Standard), and Blowfish.
The main difference between a block cipher and a stream cipher is that a block cipher works on fixed-size blocks of data or facts, while a stream cipher works on individual bits or bytes of data. So, block cipher and stream cipher have some advantages and disadvantages.
Advantages of Block Cipher
- Block cipher provides both confusion and diffusion properties, making the cipher text more efficient for cryptanalysis.
- Confusion means ciphertext bits are dependent on keystream, making it hard to find a relation between them.
- Diffusion means that each bit of the ciphertext depends on several bits of the plaintext, making it hard to find patterns in the ciphertext.
- A block cipher is more secure than stream cipher.
Disadvantages of block cipher.
- One is that it is slower than stream cipher, especially when the data is extensive or real-time encryption is required.
- Another is that it may introduce padding, which means adding extra bits to the last plaintext block to make it fit the block size. Padding can increase the size of the ciphertext and may also introduce vulnerabilities if not done correctly.
Block Cipher vs Stream
Here's a comparison table between block ciphers and stream ciphers:
Feature | Block Cipher | Stream Cipher |
Encryption | Encrypts data in fixed blocks | Encrypts data bit-by-bit/stream |
Key Management | The same key used for encryption and decryption | The same key used for encryption and decryption |
Mode of Operation | Multiple modes available | No modes required |
Performance | Slower for large data streams | Faster for real-time streams |
Key Size | Typically, larger key sizes | Typically smaller key sizes |
Vulnerability | Vulnerable to brute-force attacks if the key size is small | Vulnerable to certain attacks and weaknesses in keystream generation |
Security | Suitable for data at rest | Suitable for data in transit |
Examples | AES, DES, Triple DES | RC4, Salsa20, ChaCha20 |
FAQs
1. What are the 3 main types of cryptography algorithms?
The three main types of cryptography algorithms are:
a) Symmetric Key Algorithms
b) Asymmetric Key Algorithms (Public-Key Cryptography)
c) Hash Functions
2. What is the main weakness of block cipher?
The main weakness of a block cipher is its vulnerability to brute-force attacks, especially if the key size is not large enough. With the advancement in computing power, attackers can attempt all possible keys and decrypt the ciphertext without knowing the specific key used for encryption.
3. Is block cipher symmetric or asymmetric?
Block ciphers are generally symmetric key algorithms using the same key for encryption and decryption.
4. Is stream cipher symmetric or asymmetric?
Stream ciphers are also symmetric key algorithms, where the same secret key is used for data encryption and decryption.
5. Which is the weakest block cipher?
As technology evolves, some block ciphers become weaker due to advancements in cryptanalysis. However, DES (Data Encryption Standard) is historically considered one of the lowest block ciphers. It had a key size of only 56 bits, making it vulnerable to brute-force attacks.
6. Which cipher mode is best?
The choice of cipher mode depends on the specific use case and security requirements. Advanced Encryption Standard (AES) in Counter Mode (CTR) or Galois/Counter Mode (GCM) is often considered best for ensuring confidentiality and data integrity.
7. Which cipher is easiest?
Stream ciphers are generally easier to implement than block ciphers, primarily because they encrypt data bit by bit, making them more suitable for real-time communication.
8. Is AES a block cipher?
Yes, AES (Advanced Encryption Standard) is a block cipher.
9. Is AES a stream cipher?
No, AES is not a stream cipher. It is a block cipher.
10. Is RSA used in WhatsApp?
As of my last update in September 2021, WhatsApp primarily used the Signal Protocol, which combines the Double Ratchet Algorithm for encryption and the X3DH protocol for key exchange. RSA may be used in some capacity for authentication, but it is not the primary encryption algorithm.
11. What is the size of a block cipher?
The size of a block cipher is determined by the number of bits it processes in a single encryption or decryption operation. For AES, the block size is fixed at 128 bits.
12. What are the two types of encryption?
The two main types of encryption are:
a) Symmetric encryption: Uses the same secret key for encryption and decryption.
b) Asymmetric encryption: Uses a pair of keys - a public key for encryption and a private key for decryption.
13. What is the key size of a block cipher?
The key size of a block cipher refers to the length of the secret key used in the encryption process. For AES, the commonly used key sizes are 128, 192, and 256 bits.
14. What is the fastest cipher?
The speed of a cipher depends on the specific hardware and software implementations. However, symmetric ciphers like AES with a 128-bit key are generally known for their fast encryption and decryption speeds.
15. What is the hardest cipher to crack?
A cipher's difficulty to crack depends on key size, algorithm strength, and the absence of vulnerabilities. In the context of widely accepted cryptographic algorithms, AES with a 256-bit key is currently considered one of the hardest ciphers to crack.
16. What is the most famous cipher?
As of my last update in September 2021, AES (Advanced Encryption Standard) was the most popular and widely used symmetric encryption algorithm worldwide.
17. Is SSL a stream cipher?
SSL (Secure Sockets Layer) is not a cipher but a cryptographic protocol to secure communication over a computer network. However, it can work with various cipher suites including block and stream ciphers.
18. Is RSA also a stream cipher?
No, RSA is not a stream cipher; it is an asymmetric encryption algorithm for secure key exchange and digital signatures.
19. Why is RC4 a stream cipher?
RC4 is a stream cipher because it encrypts data bit by bit or byte by byte, generating a keystream combined with the plaintext using XOR to produce the ciphertext.
Conclusion
In this article, we have discussed block cipher vs stream cipher. In conclusion, block cipher and stream cipher are symmetric encryption techniques with different characteristics and applications. A block cipher is more suitable for applications that require strong encryption, such as file storage and internet communications. A stream cipher is ideal for applications requiring fast encryption, such as voice and video streaming and wireless communications. Both techniques have their strengths and weaknesses, and choosing the right one depends on each scenario's security requirements and performance constraints.